|
|
|
| This document is available in: English Castellano Deutsch Francais Italiano Nederlands Portugues Russian Turkce |
![[Photo of the Author]](../../common/images/Georges-Tarbouriech.jpg)
by Georges Tarbouriech About the author: Georges is a long time Unix user. He thinks computer security is
one of main challenges of this century. Content: |
![[illustration]](../../common/images/illustration214.jpg)
Abstract:
Psionic portsentry is part of the Abacus Project suite of tools (beside portsentry, the suite offers logcheck and hostsentry). It's an IDS (Intrusion Detection System) dedicated to portscan detection and active defense. It works on many Unix flavors including Mac OS X. The main feature of an IDS is to inform the sysadmin about intrusion attempts. Portsentry goes further since it can react on an attack. The latest version (1.1) of this great tool is available from http://www.psionic.com, and by the way, version 1.0 is now part of some main Linux distributions (Debian, RedHat...).
During the last decade, networking grew up at an incredible speed. The goal
was to allow communication between machines using different OSes. Thus,
proprietary networking systems were slowly replaced with TCP/IP. Internet
did the rest ! Today, most networking relies on TCP/IP and TCP/IP relies on ports.
To make it short, ports are attached to programs (clients or servers). The
server listens till a client contacts it to establish a connection. The
services (the programs above mentioned) are mapped to a specific port. On
Unix systems, this mapping scheme is found in the /etc/services file. That
is, everyone knows which port is dedicated to which service. If everyone
knows, crackers know even better ! If we consider a port as a door, when a
port is open (listening), it's like an unlocked door. And how do you get
into a house ? Usually through the door (unless you prefer the window, it's
up to you !). So do the black hats to get into your computer...
The first thing you can do to reduce the risk is to close as many ports as
possible, that is to stop services. The less the better. But you hardly can
close every port on a networked machine : it wouldn't communicate
anymore, that would be a pity !
How to limit the number of active services
or how to close the ports is beyond the scope of this article. You'll find a
lot of literature on the subject, for instance going to the Linux Documentation Project or searching
through LinuxFocus issues (for example, Bastille Linux or Security tools). So for the different ways to protect a machine,
a network. On Linux, consider Bastille Linux as a must have.
And this is where portsentry comes. Portsentry can monitor ports
and is able to block them if you ask it to do so. It provides you with
different operating modes, some of them being specific to some OSes. As a
matter of fact, OSes means Linux.
Portsentry is able to benefit
from packet filtering provided with ipfwadm, ipchains or iptables according
to the Linux kernel you have. This is true for other Unix flavors using
different tools (back on this later). There we are : portsentry greatest feature
probably is "auto-blocking".
How does it manage that ? Here we go !
Portsentry comes as a very small tarball. After unpacking the archive, you
get source code and various configuration and README files. Obviously, all
that stuff is recommended reading. Since we're talking about security, don't
forget to download the PGP files (signature and key).
Installing portsentry is obvious : make (your system) and make install. But
before installation, you should prepare it. That is, you should read the
documentation, change the portsentry.conf file to suit your needs and check
the Makefile as well as the portsentry_config.h file.
For portsentry to be the most efficient, you need at least TCPWrappers. At
least, because it would be much better to use it in conjunction with a
packet filtering tool. Of course, if you use Linux, you already have
everything you need. What about other Unices ?
Since we tested portsentry on different platforms, let's talk about the
requirements.
On MAC OS X, it's like for Linux : everything is there. You have TCPWrappers,
and ipfw (the BSD version). So just typing "make osx" will do
the trick.
On Solaris 2.6 (SPARC), you don't have TCPWrappers. You can get it from ftp://ftp.porcupine.org/pub/security.
You can also try IPFilter available from ftp://coombs.anu.edu.au/pub/net/ip-filter/ip-fil3.4.9.tar.gz
(but only if you have the Solaris compiler !!!).
On Irix 6.5, you don't have TCPWrappers either. You can get it as a package from
http://freeware.sgi.com/index-by-alpha.html
For packet filtering you have ipfilterd, coming with Irix but not installed by
default.
Last, but not least, unless you find a working vsnprintf(), you won't be able to
install portsentry on NeXTSTEP... and I didn't find one !
However, once again, you should configure portsentry before installing it. Well,
it's up to you, but it should be better to understand its philosophy before
everything else... but it's just a matter of opinion !
Fine, thank you !
More seriously, portsentry relies on configuration files. The most important is
the portsentry.conf file. This is where you tell portsentry how to react against
adversity.
Before dealing with that file, you need to know what the different modes of
operations are and what they do.
Portsentry can use six different modes, according to the option you give at
startup.
- The first one is "-tcp" and it is the basic mode. With this option,
portsentry will bind the TCP ports found in the config file in the "port
configuration" section. It can bind till the limit of 64 ports.
- The second one is "-udp" and does the same as the previous one for UDP ports.
- The third is "-stcp", the "s" meaning stealth. This option and the next ones are
only available for Linux. With the "-stcp" option, portsentry uses a socket to
monitor incoming packets, that is the ports are not binding to anything.
- The fourth is "-sudp" and does the same as the previous one for UDP ports.
- The fifth and sixth are "-atcp" and "-audp". These are the most effective
options ("a" stands for advanced). Using these options, portsentry makes a list
of the listening ports, TCP and UDP, if you select both, and blocks the host
connecting to these ports, unless this host is present in the portsentry.ignore
file.
This is much better explained in the README files coming with portsentry.
Accordingly, we won't reinvent the wheel, trying to rewrite the documentation.
These README files are compulsory reading (as usual, let's be a bit fascist !).
Obviously, portsentry can generate logs. If you are the kind of sysadmin not reading the
logs (shame on you !), you can use logcheck in conjunction with portsentry.
That way, portsentry sends a mail to inform you about an intrusion attempt.
It can write the target host into the /etc/hosts.deny file, for use with
TCPWrappers.
The local host is able to route the network traffic to a dead host.
Last, the local host can drop the packets through the packet filtering local
tool.
Now you know a bit better about portsentry philosophy, you can start
writing your portsentry.conf file.
- The first section of the config file concerns the ports. There, you can choose
the ports to bind. Remember, this is ignored when using the advanced
modes for Linux. Careful with the ports you want to bind (don't bind port 6000
if you use X, for instance).
- The next section is for advanced detection options. The default is to
monitor every port below 1024, either for TCP or UDP. There, you can
also exclude the ports you wish to ignore. This is quite important to
avoid false alarms, and so huge logging, especially if you have Windos
machines in your network. For instance, mind the port 111 if portmap is
used and the hosts are not present in the portsentry.ignore file. Sure,
it would be crazy, since portmap means RPC servers like NFS, but you've
been warned. That is, NFS is not that secure on Unix machines so don't
we talk about Windos machines.
Here comes the usual off-topic section : when I
write "Windos", it is not a typo : it is just to insist on the fact Windows is
a desktop environment on top of DOS (D for dirty ?)... and it makes one less
character to type (how lazy I am !). Sorry for the digression.
- The configuration files section concerns the files used by portsentry for
history purpose or to define the hosts to ignore. If you
perform a default install, don't change this.
- The miscellaneous config section allows to turn on or off DNS lookups.
- The response options section is the heart of the configuration. This is where
you define how portsentry will react.
First, are the ignore options. You can choose to block the scans, not to block
them or run an external command.
Next, in the dropping routes section, you tell portsentry how to drop the route
or how to benefit from the packet filtering tool used on your machine.
There are a lot of examples for many platforms. Select the one (and only one !) suiting your
needs.
- The TCPWrappers section indicates if you want to write into the /etc/hosts.deny
file.
- The external commands section allows to define a command to run when an host
connects.
- The scan trigger value section allows to define the reaction time. The default
value of "0" is the most immediate since it sends an alarm at first connection
attempt.
- The last section is to display a banner in case of intrusion attempt. It doesn't
work with stealth modes.
When finished with that part, you're almost done. Again to avoid false alarms
and huge logging, check the portsentry.ignore file. You can add there your local
network address with netmask bits, or the IP address of a few machines.
That's it ! You can now "make yoursystem" and "make install". The install script
does the whole job since it gives restricted permissions to the directory and the
files. Now, enough to run portsentry with the options of your choice.
Check the logs to see what happened. If everything went well, portsentry has
started and has hardened the host security.
Using tools such as nmap, you may now simulate a port scan of your newly secured host. (More on nmap there). This is the answer you can get :
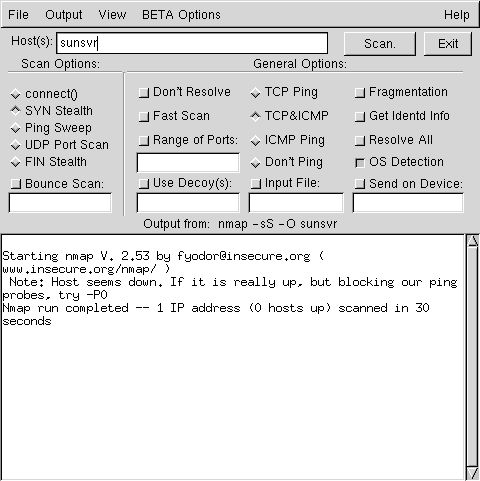
Definitely NOT ! There are a lot of IDS, free or not. Most of them are quite
good. Let's mention the well known snort, available from http://www.snort.org.
Usually, those IDSes are passive ones. That is, they are used to inform you about
intrusion. That's what they have been made for. For instance, snort is quite
sophisticated, since it relies on rules scripts, thus allowing you to write your
own. Snort website also provides a rules database. And, by the way, if you aren't afraid of
huge logs, you can even run both portsentry and snort. It isn't that silly !
However, the strength of portsentry is that it is an active IDS. The way it can
react is really breathtaking. Combining it with a packet filtering tool, makes it
the mandatory tool. We could ask the question : is portsentry the complement of
packet filter or is packet filter the complement of portsentry ?
Anyway, there's a lot more we could say about portsentry. For
instance, you must be very careful with advanded mode UDP scan
detection. Do read the doc (again !) to
understand the problems related to UDP. Solaris may cause some problems
as well,
since it uses very high ports in the 32700 range (either TCP or UDP).
But, this article is only an
overview and in no way a complete review of this great piece of
software.
Computer security is a concern, and not only for sysadmin. The incredible growth
of the Internet makes things worse. That is, the danger of intrusion is
everyday bigger. The free software community provides us with great tools :
portsentry is one of them. Don't leave them aside ! But, remember, these tools
only reduce the risk and in no way provides you with a 100% secure system.
This is another reason to investigate the security tools area.
Last, but not least, people at Psionic are working on a commercial product and
tell us "we won't be disappointed". Wait and see, then !
In the meantime, go and get portsentry 1.1, you won't be disappointed either.
People at Psionic do a great job. By the way, hostsentry is also worth
testing... and using.
We are living in a great time, aren't we ?
The following websites are absolute references when security is concerned.
Furthermore, they can send you to some more websites, those last sending you to
some more websites... You know, the Russian dolls ? The only trouble if you want
to read the whole stuff is that you won't live long time enough !!!
http://www.linuxsecurity.com
http://www.sans.org
http://www.infosyssec.org
http://www.securityfocus.com
http://www.cs.purdue.edu/coast/hotlist/
|
|
Webpages maintained by the LinuxFocus Editor team
© Georges Tarbouriech, FDL LinuxFocus.org Click here to report a fault or send a comment to LinuxFocus |
2001-08-21, generated by lfparser version 2.17